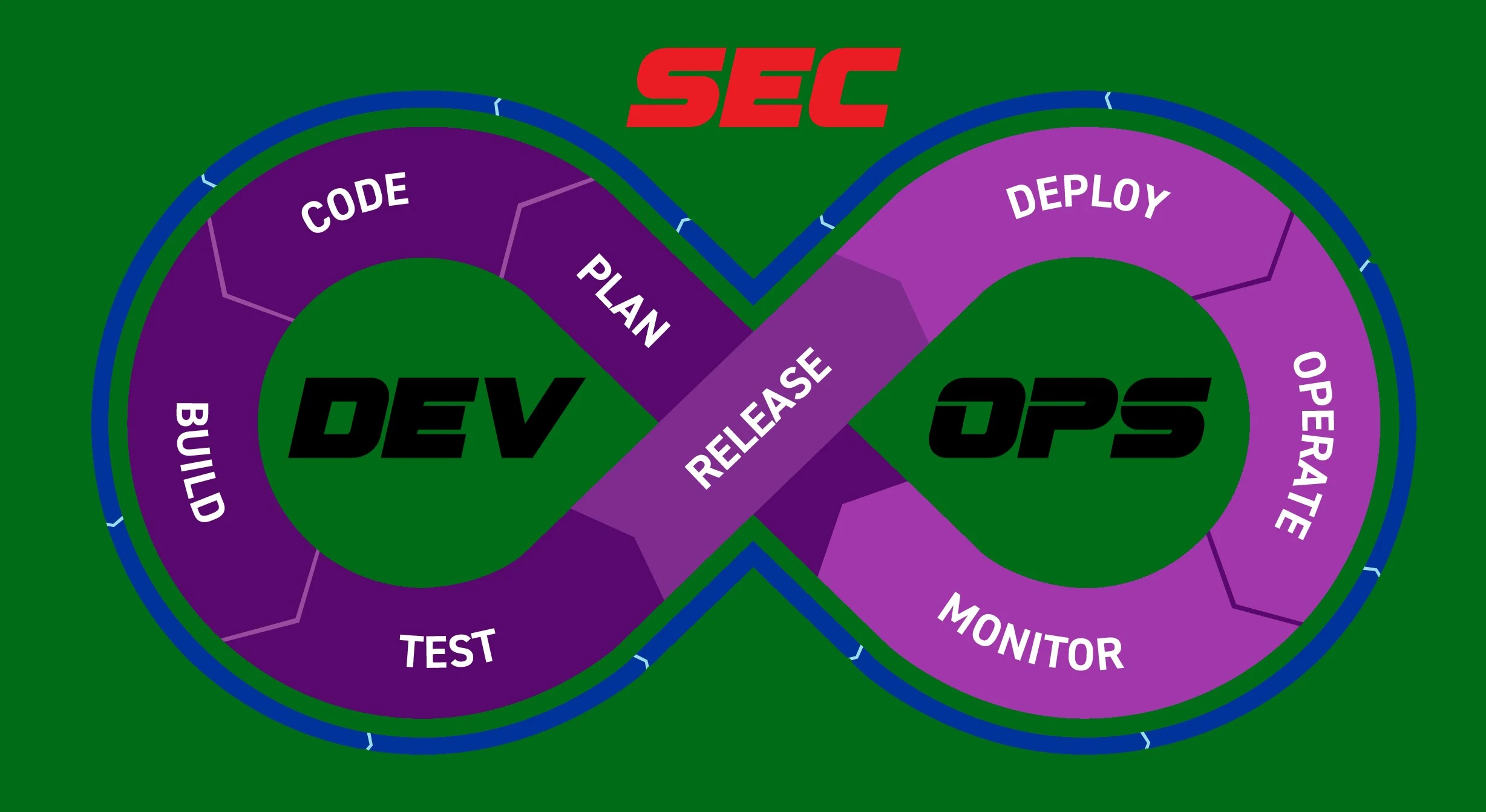
DevSecOps is a term that combines development, security and operations. It is an approach that integrates security into every phase of the software development life cycle (SDLC), from initial design to deployment and delivery.
- Introduction
- Body
- Discuss the main principles and practices of DevSecOps:
- Shift left security: Incorporate security into the early stages of the SDLC:
- What are some examples of shift left security tools?
- What are some best practices for integrating shift left security tools into CI/CD pipelines?
- Automate Security Tasks:
- What are some examples of security automation tools?
- Collaborate &Communicate:
- How to measure the effectiveness of your collaboration and communication practices?
- What are some common challenges of implementing a DevSecOps culture?
- What are some best practices for integrating security into agile development?
- What are some common security vulnerabilities in agile development?
- Discuss the main principles and practices of DevSecOps:
- Conclusion
Introduction
It's aims to produce more secure code more quickly by automating security tasks and fostering a culture of collaboration among teams. But why is DevSecOps so important for modern software development?
In this blog post, we will explore the benefits of this topic and how you can implement it in your organization.
Software development has changed dramatically in recent years, thanks to the emergence of cloud platforms, microservices, containers and agile methodologies. These technologies enable developers to create and deploy applications faster and more frequently, meeting the ever-changing needs and expectations of customers.
However, this also poses new challenges and risks for security. Traditional security practices such as manual testing and audits. They create bottlenecks and delays in the DevOps process, compromising the quality and reliability of the software. Moreover, they expose the software to cyberattacks, data breaches and compliance violations which can damage the reputation and revenue of the organization.
Challenges
DevSecOps addresses these challenges by embedding security into the DevOps process and making it an integral part of the software development life cycle. By applying security best practices from the start, DevSecOps helps developers identify and fix vulnerabilities earlier when they are easier and cheaper to resolve.
And also leverages automation tools and frameworks to perform security checks, scans and audits throughout the DevOps pipeline and ensuring that the software meets the security standards and regulations.
Furthermore, it promotes a culture of shared responsibility and trust among developers, security engineers and operations teams.
Benefits of DevSecOps
The benefits of it are evident in many statistics and examples. According to a report by Puppet Labs, organizations that practice DevSecOps are 24 times more likely to deploy code on demand than those that do not. They are also 22 percent more likely to have met or exceeded their organizational performance goals.
As you can see, DevSecOps is not just a buzzword or a trend. It is a necessity for modern software development.
Body
Discuss the main principles and practices of DevSecOps:
Shift left security: Incorporate security into the early stages of the SDLC:
One of the main principles of DevSecOps is shift left security. This means incorporating security into the early stages of the SDLC such as design, coding and testing. Shift left security helps developers identify and fix vulnerabilities as they write the code, rather than waiting for the testing or deployment phase. This reduces the risk of releasing insecure or non-compliant software, as well as the cost and time of fixing security issues later in the process.
It requires a change in mindset and culture, as well as the use of tools and frameworks that support security automation and integration.
Some of the best practices for implementing shift left security are:
- Educate developers on security best practices and standards such as secure coding guidelines, threat modeling and risk assessment.
- Use security plugins and extensions in the integrated development environment (IDE) to provide real-time feedback and suggestions to developers as they code.
- Incorporate security testing tools and frameworks into the continuous integration (CI) and continuous delivery (CD) pipelines such as static application security testing (SAST), dynamic application security testing (DAST), software composition analysis (SCA) and interactive application security testing (IAST).
- Enable continuous feedback loops and collaboration between developers, security engineers and operations teams by using tools such as chatbots, dashboards and alerts.
- Monitor and measure the security performance and outcomes of the its process by using metrics such as mean time to detect (MTTD), mean time to resolve (MTTR), vulnerability density and compliance rate.
What are some examples of shift left security tools?
- Software Composition Analysis (SCA): These tools scan the code for open-source components and dependencies and identify any known vulnerabilities or license issues in them.
- Static Application Security Testing (SAST): These tools analyze the source code or binaries for common security weaknesses, such as injection flaws, cross-site scripting, or buffer overflows.
- Dynamic Application Security Testing (DAST): These tools simulate attacks on the running application or web service and detect any security vulnerabilities or misconfigurations in the runtime environment.
- Interactive Application Security Testing (IAST): These tools combine the features of SAST and DAST and monitor the application behavior and data flow during testing or normal usage and report any security issues in real time.
- Secrets Detection: These tools scan the code repositories and configuration files for any sensitive information, such as passwords, API keys, tokens, or certificates, and alert the developers to remove or encrypt them.
- Software Composition Analysis (SCA): These tools scan the code for open-source components and dependencies and identify any known vulnerabilities or license issues in them.
These are some of the tools that can help developers shift security left in the SDLC. However, tools alone are not enough. Developers also need to follow security best practices and standards, collaborate with security engineers and operations teams and continuously monitor and improve the security performance of their applications.
What are some best practices for integrating shift left security tools into CI/CD pipelines?
Choose the right tools for your needs and environment:
There are many types of shifts left security tools such as: SAST, DAST, IAST, SCA and secrets detection. You should evaluate the features, compatibility and performance of these tools and select the ones that suit your application type, language, framework and platform.
Automate the security testing process:
You should integrate the security tools into your CI/CD pipeline using plugins, scripts or APIs. This way, you can ensure that the security testing is performed automatically and consistently every time the code is committed, built or deployed.
Configure the security testing parameters and thresholds:
Define the scope, frequency and depth of the security testing according to your risk appetite and compliance requirements. And also set the criteria for passing or failing the security tests such as: the number or severity of vulnerabilities allowed.
Provide feedback and remediation guidance to developers:
Make the security test results visible and accessible to developers through dashboards, reports or alerts. And provide clear and actionable recommendations on how to fix the security issues detected by the tools.
Monitor and measure the security outcomes and improvements:
Track and analyze the security metrics and trends over time such as: the vulnerability density, remediation rate, mean time to detect (MTTD), mean time to resolve (MTTR) etc. And use these metrics to evaluate the effectiveness of your shift left security tools and practices.
By following these best practices, you can integrate shift left security tools into your CI/CD pipelines and improve your application security posture.
Automate Security Tasks:
Another main principle of DevSecOps is Automate Security Tasks. This means using tools and frameworks to automate security checks, scans and audits throughout the DevOps pipeline. Automating security tasks helps developers save time and effort, reduce human errors and ensure consistent and continuous security testing across the SDLC.
Some of the benefits of automating security tasks are:
- Faster and more frequent releases with less security risks.
- Higher code quality and reliability with fewer defects and vulnerabilities.
- Improved collaboration and communication between developers, security engineers and operations teams.
- Reduced costs and time for fixing security issues.
- Enhanced compliance with security standards and regulations.
What are some examples of security automation tools?
Security Information and Event Management (SIEM): SIEM solutions are designed to collect, aggregate and analyze security data from across an organization’s IT environment. They can help automate the detection and correlation of security events, generate alerts and reports and support incident response and forensics.
Security Orchestration, Automation and Response (SOAR): SOAR solutions are platforms that integrate various security tools and processes and enable the automation and orchestration of security workflows. They can help automate the execution of security playbooks, facilitate collaboration and communication among security teams and provide metrics and dashboards to measure security performance.
Extended Detection and Response (XDR): XDR solutions are platforms that provide unified visibility and protection across multiple security domains such as: endpoints, networks, clouds and applications. They can help automate the collection and analysis of security data from different sources, apply advanced threat detection and response capabilities and streamline security operations.
Security Testing Tools: Security testing tools are tools that perform various types of security tests on applications such as: SAST, DAST, IAST, SCA and secrets detection. They can help automate the identification and remediation of security vulnerabilities in the code or the runtime environment.
Security Automation Frameworks: Security automation frameworks are tools that provide a set of libraries, modules, or scripts to automate common security tasks or scenarios. They can help simplify the integration and configuration of security tools, customize the automation logic and workflows, and reuse the existing code or templates.
Collaborate &Communicate:
This means fostering a culture of shared responsibility and trust among developers, security engineers and operations teams. Collaborate and communicate also involves using feedback loops and metrics to monitor and improve security performance.
Some of the benefits of collaborating and communicating are:
- Improved alignment and coordination among teams with different goals, skills, and perspectives.
- Increased awareness and visibility of security issues and risks across the SDLC.
- Enhanced learning and knowledge sharing among team members.
- Reduced silos and conflicts that can hinder security effectiveness and efficiency.
- Increased agility and innovation in delivering secure and high-quality software.
How to measure the effectiveness of your collaboration and communication practices?
To measure the effectiveness of your collaboration and communication practices, you need to define and track some key performance indicators (KPIs) that reflect the quality and outcomes of your team interactions. Some examples of collaboration and communication KPIs are:
Employee engagement index: This metric measures how engaged and motivated your team members are in their work and in the organization. It can be calculated by using surveys, feedback or behavioral data such as attendance, retention, productivity etc. A high employee engagement index indicates a positive and collaborative work culture.
Employee satisfaction index: This metric measures how satisfied and happy your team members are with their work environment, conditions and relationships. It can be calculated by using surveys, feedback or ratings, such as net promoter score (NPS), employee satisfaction score (ESAT) etc. A high employee satisfaction index indicates a supportive and communicative work culture.
Manager quality index: This metric measures how effective and competent your managers are in leading and supporting their teams. It can be calculated by using surveys, feedback or ratings from team members, peers or senior leaders. A high manager quality index indicates a strong and trustworthy leadership culture.
HR effectiveness index: This metric measures how efficient and responsive your HR department is in providing services and solutions to your team members. It can be calculated by using surveys, feedback or metrics such as time to hire, time to onboard, time to resolve issues etc. A high HR effectiveness index indicates a smooth and collaborative HR culture.
What are some common challenges of implementing a DevSecOps culture?
Lack of security assurance at the business and project levels: Security is often seen as a technical issue, rather than a business or project issue. This can lead to a lack of security awareness, buy-in and support from senior leaders, stakeholders and customers. Security requirements and expectations may not be clearly defined, communicated or aligned with the business goals and customer needs.
Organizational barriers related to collaboration, tooling and culture: Security is often siloed from development and operations, resulting in poor communication, coordination and trust among teams. Security tools and processes may not be compatible or integrated with the DevOps tools and processes, causing friction and delays. Security culture may not be consistent or positive across the organization, leading to resistance or indifference to security practices.
Impact to quality because security is not a priority while systems are getting more complex: Security is often deprioritized or neglected in favor of speed and functionality, especially in agile and iterative development environments. Security testing and remediation may be postponed or skipped, leaving security vulnerabilities unaddressed. Systems are getting more complex and distributed, increasing the attack surface and the difficulty of securing them.
Lack of security skills for developers, business stakeholders and auditors: Developers may not have sufficient security knowledge or skills to perform security tasks or to understand the security implications of their actions. Business stakeholders and auditors may not have sufficient technical knowledge or skills to assess the security risks or compliance of the systems. Security training and education may be inadequate or unavailable for these roles.
Insufficient security guidance due to lack of resources, standards and data: Security guidance may be scarce, outdated or inconsistent due to a lack of resources, standards and data. Security policies, procedures and best practices may not be well-defined, documented or enforced. Security metrics and feedback may not be collected, analyzed or reported effectively. Security decisions may be based on assumptions, opinions or preferences rather than on evidence.
What are some best practices for integrating security into agile development?
Add security acceptance criteria in user stories:
Capture unique security criteria that are not covered by cross-functional requirements in stories and validate these in the QA process. For example, you can specify the security level, encryption method, authentication mechanism or compliance standard for each user story.
Conduct various security tests during product review:
Perform different types of security tests, such as SAST, DAST, IAST, SCA and secrets detection, during the product review phase of each iteration. Use automation tools and frameworks to speed up the testing process and provide feedback to developers.
Develop proper code conventions for OWASP Proactive Controls:
Follow the OWASP Proactive Controls, which are a set of security best practices for developers to prevent common web application vulnerabilities. Develop proper code conventions and guidelines based on these controls and enforce them throughout the development process.
Use Agile Retrospectives:
Use Agile Retrospectives to reflect on the security performance and outcomes of each iteration. Identify what went well, what went wrong, and what can be improved in terms of security practices, tools and processes. Implement the improvement actions in the next iteration.
Integrate Continuous Integration Security Practices in the SDLC:
Integrate security practices into the continuous integration (CI) process of the SDLC.
For example, you can use pre-commit hooks to check the code quality and security before committing it to the repository. You can also use post-commit hooks to trigger security scans and audits after committing the code.
Build security into your pipeline:
Build security into your continuous delivery (CD) pipeline by using tools and frameworks that support security automation and orchestration.
For example, you can use tools such as Jenkins, Ansible, Chef or Puppet to automate the deployment of security configurations and patches. You can also use tools such as GitLab, GitHub or Azure DevOps to orchestrate the security workflows and tasks.
What are some common security vulnerabilities in agile development?
Insufficient policies governing the use of open-source components:
The core principle of Agile is to discourage re-inventing the wheel. Additionally, teams are encouraged to include open-source and commercial proprietary solutions to shorten development lifecycles. However, these components may introduce security risks if they are not properly vetted, updated or configured.
For example, they may contain known vulnerabilities, malicious code or incompatible licenses.
Rapid release cycle:
Agile development aims to deliver working software in short and frequent iterations. However, this may compromise security if security testing and remediation are not performed adequately or timely.
For example, security issues may be overlooked, ignored or deferred in favor of functionality or speed.
Emergence of new threats:
Agile development involves constant changes and adaptations to meet the evolving needs and expectations of customers and stakeholders. However, this also means that the security landscape is constantly changing, and new threats may emerge that were not anticipated or addressed in the previous iterations.
For example, new features, integrations or platforms may introduce new attack vectors or vulnerabilities.
Inadequate security awareness and training:
Agile development requires developers to take more responsibility for security tasks and decisions. However, developers may not have sufficient security knowledge or skills to perform these tasks or to understand the security implications of their actions.
For example, they may not follow secure coding practices, use insecure tools or frameworks, or implement weak encryption or authentication mechanisms.
Unlimited access to source code repositories and CI/CD pipelines:
Agile development relies on collaboration and automation tools such as source code repositories and continuous integration and continuous delivery (CI/CD) pipelines. However, these tools may pose security risks if they are not properly secured and monitored.
For example, unauthorized or malicious users may access, modify or delete the source code or the configuration files, compromising the integrity or availability of the software.
Failure to manage sensitive data:
Agile development involves collecting, processing, and storing various types of data from customers, users, or third parties. However, this data may be sensitive or confidential and require special protection and handling.
For example, personal data, financial data, health data, or intellectual property data may be exposed, leaked or breached if they are not encrypted, anonymized or deleted when no longer needed.
These are some of the security vulnerabilities that can affect agile development. However, these vulnerabilities can be prevented or mitigated by adopting some best practices such as:
- Establishing clear policies and procedures for using open-source components.
- Conducting various security tests during product review.
- Developing proper code conventions for OWASP Proactive Controls.
- Using Agile Retrospectives to reflect on the security performance and outcomes.
- Integrating Continuous Integration Security Practices in the SDLC.
- Building security into your pipeline.
By following these best practices, you can improve your security posture in agile development and deliver more secure and high-quality software.
Conclusion
DevSecOps is the integration of security into the agile development process. It involves the collaboration between development, security, and operations teams to build security into every aspect of the software development lifecycle. By doing so, security becomes an essential part of the development process rather than an afterthought.
If you want to learn more about DevSecOps, you can check out these resources:
DevSecOps: How to Seamlessly Integrate Security Into DevOps | Splunk
DevSecOps: The Key to Cloud Security | Microsoft Azure
DevSecOps: 5 Best Practices to Enable Secure DevOps | Rapid7 Blog
How to Automate Security Testing for DevSecOps | GitLab
What are some of the challenges or benefits of DevSecOps that you have experienced or observed in your organization? Share your thoughts in the comments below.